Mobile apps are the backbone of modern startups. They provide a platform for businesses to reach customers on the go, and they are essential for streamlining operations and facilitating communication. But with the rise of cyber threats, mobile app security has become a major concern for startup founders and entrepreneurs. Cyber-attacks can compromise sensitive user data, damage brand reputation, and even result in legal consequences. Therefore, it’s crucial to prioritize mobile app security when developing your startup’s app. In this guide, we will explore the best practices for keeping your mobile app safe from cyber-attacks.
What is mobile app security?
Mobile app security refers to the measures taken to protect mobile applications from unauthorized access, theft, or malicious attacks.
It involves implementing various security practices and technologies to safeguard sensitive data, such as personal information, financial details, and login credentials, that may be stored on a mobile device or transmitted between the app and a server.
Mobile app security is important to prevent cyber-attacks that can compromise user data, and cause harm to both the user and the startup owners, or to the entrepreneurs who developed the app.
To emphasize why mobile app security is so crucial, let’s look at some relevant stats.
- 82% of Android devices were susceptible to at least one out of 25 vulnerabilities in the Android operating system.
- Business apps are three times more likely to leak log-in credentials (both personal and corporate data) than the average app.
- One in four mobile applications contains at least one high-risk security flaw.
- 50% of apps with five to ten million downloads include a security flaw.
- 25% of the 2 million applications available on Google Play alone include a security flaw.
As a result, the focus is to shift toward safeguarding mobile applications in a way that does not interfere with the app’s look and feel. The ultimate goal is to be able to detect and prevent mobile application attacks in real-time.
“Mobile app security must be a proactive measure, not a reactive measure.”
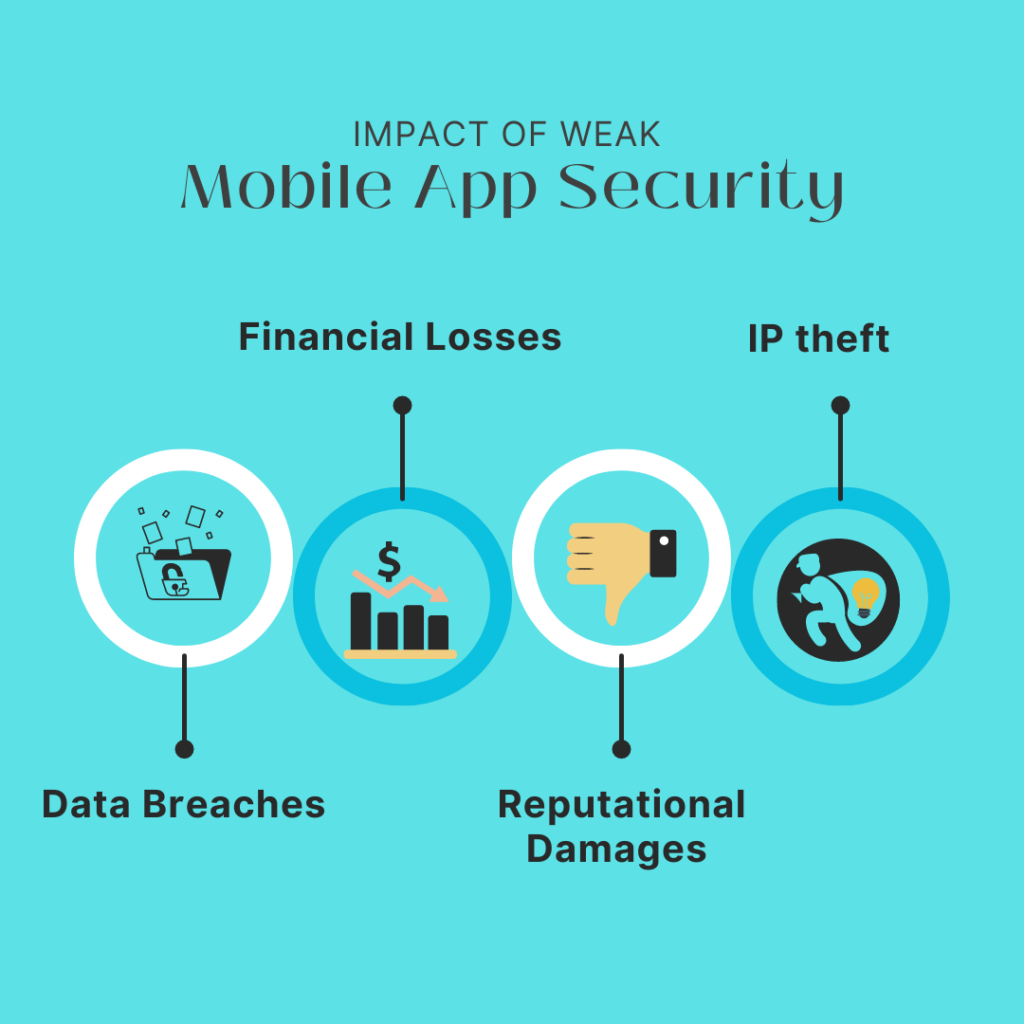
Impact of weak mobile app security
Weak mobile app security can have severe consequences for users and businesses alike. Inadequate security measures can lead to data breaches & financial losses. Users may have their personal information stolen, which can be used for identity theft and other criminal activities. Additionally, businesses may be liable for legal and regulatory penalties resulting from data breaches, which can be costly and damaging to their reputation.
- Data breaches: When sensitive user data is stolen, leaked, or accessed by unauthorized parties. For example, the 2013 Target data breach, where hackers gained access to the personal and financial information of over 110 million customers.
- Financial losses: When users or businesses lose money as a result of fraudulent activities. For example, the 2016 Bangladesh Bank cyber heist, where hackers stole $81 million by exploiting vulnerabilities in the bank’s mobile app.
- Reputational damage: When a company’s brand or reputation is harmed due to security breaches. For example, the 2017 Equifax data breach, where hackers stole sensitive personal information from over 147 million customers, resulted in a severe loss of trust and reputation for the company.
Loopholes in mobile app security
There are several common loopholes in mobile app security that hackers can exploit. Some examples of these loopholes include:
Poor authentication: Weak authentication mechanisms such as easily guessable passwords or no two-factor authentication can make it easier for hackers to gain access to user accounts and data. For example, the 2014 Snapchat data breach, where hackers gained access to over 4.6 million usernames and phone numbers due to weak authentication mechanisms.
Insecure data storage: Storing sensitive data on a device’s local storage or in an insecure cloud environment can put users’ data at risk. For example, the 2014 iCloud data breach, where hackers gained access to personal photos and videos of several celebrities due to insecure data storage.
Inadequate encryption: Lack of encryption protocols or weak encryption can make it easier for hackers to intercept and steal user data. For example, the 2014 Heartbleed bug, which affected many mobile apps and websites, allowed hackers to intercept and steal sensitive user data due to inadequate encryption.
Vulnerable code: Security vulnerabilities in the code of mobile apps can be exploited by hackers to gain access to user data and exploit weaknesses in the app. For example, the 2015 Stagefright bug, which affected over a billion Android devices, allowed hackers to gain access to user data and control devices due to a vulnerability in the code of the messaging app.
Android app security risks
Android apps are particularly vulnerable to security risks due to the open-source nature of the platform and the high level of fragmentation in the Android ecosystem. Some examples of Android app security risks include:
- Malware: Android devices are particularly susceptible to malware due to a large number of third-party app stores and the ability to side-load apps from non-official sources. For example, the 2015 HummingBad malware, which affected over 85 million Android devices, allowed hackers to take control of the device and steal user data.
- Permission issues: Android apps often require access to sensitive user data and features, such as the camera or microphone, and users may not always be aware of what permissions they are granting. This can result in apps having access to more data than necessary, putting user privacy at risk. For example, the 2018 Cambridge Analytica scandal, where a third-party app accessed and harvested personal data from Facebook users without their consent.
- Fragmentation: Due to the wide range of Android devices and operating system versions, it can be challenging to maintain consistent security standards across all devices. This can result in security vulnerabilities that affect specific devices or versions of the operating system, making it difficult for startup owners and entrepreneurs to ensure the security of their apps on all Android devices.
- Man-in-the-middle attacks: Android apps can be vulnerable to man-in-the-middle (MITM) attacks, where attackers intercept the communication between the app and the server to steal sensitive information. For example, the 2019 StrandHogg vulnerability allowed attackers to hijack legitimate Android apps to steal user data and credentials.
- Code vulnerabilities: Android apps can also be vulnerable to code vulnerabilities, such as buffer overflows or SQL injection attacks, which can be used to exploit the app and gain access to user data. For example, the 2015 Stagefright vulnerability allowed attackers to execute arbitrary code on Android devices by sending a malicious multimedia message (MMS).
- Third-party libraries: Many Android apps use third-party libraries to add functionality or save development time, but these libraries can also contain vulnerabilities that can be exploited by attackers. For example, the 2015 XcodeGhost malware campaign used a compromised version of the Xcode development environment to inject malicious code into Android apps that used the library.
iOS app security risks
While iOS devices are generally considered more secure than Android devices, there are still risks associated with iOS app security. Some examples of iOS app security risks include:
- Jailbreaking: Users can jailbreak their iOS devices to bypass restrictions imposed by Apple and install unauthorized apps, which can contain malware or other security risks.
- Insecure app stores: While the Apple App Store is generally considered safe, third-party app stores can pose security risks. Users may unknowingly download apps from untrusted sources, which can contain malware or other security vulnerabilities.
- Phishing attacks: iOS apps can be vulnerable to phishing attacks, where attackers try to trick users into providing sensitive information such as usernames and passwords. For example, the 2016 iOS phishing attack, where attackers created a fake login page for iCloud and tricked users into providing their login credentials.
- In-app purchases: In-app purchases can be a source of risk for iOS apps, as attackers can use fake or compromised App Store accounts to make fraudulent purchases. This can result in financial losses for the app developer and damage to the reputation of the app.
- Keychain vulnerabilities: The iOS keychain is used to securely store sensitive data, such as passwords and certificates, but vulnerabilities in the keychain can be exploited by attackers to steal this data. For example, the 2015 KeyRaider malware campaign targeted jailbroken iOS devices to steal Apple ID credentials and certificates from the keychain.
- Social engineering: iOS apps can be vulnerable to social engineering attacks, where attackers try to trick users into revealing sensitive information or installing malicious apps. For example, the 2017 Fake WhatsApp app, which masqueraded as a legitimate messaging app, was used to distribute malware and steal user data from iOS devices.
Common mobile application risks that both Android and iOS platforms face:
- Malicious code injection: This is a common technique used by attackers to inject malicious code into a mobile application to steal sensitive data or gain unauthorized access to the device. Attackers can inject malicious code into an application by exploiting vulnerabilities in the application or the mobile operating system.
- Lack of encryption: Mobile applications often handle sensitive data such as user credentials, credit card details, and personal information. If this data is not encrypted, it can be easily intercepted and stolen by attackers. Both Android and iOS platforms provide encryption APIs that developers can use to encrypt sensitive data, but many apps do not use them properly.
- Binary planting: Also known as DLL hijacking, this is a technique used by attackers to inject malicious code into an application by replacing a legitimate binary with a malicious one. This can happen if the application loads a library or framework from an untrusted location.
- Mobile botnets: Botnets are networks of compromised devices that can be controlled by attackers to perform malicious activities such as DDoS attacks or mining cryptocurrency. Mobile botnets are becoming increasingly common, as attackers can use them to launch attacks on other devices or steal sensitive data from the compromised device.
- Insecure data storage: Mobile applications often store sensitive data on the device, such as login credentials or personal information. If this data is stored in an insecure manner, it can be easily accessed by attackers. Both Android and iOS platforms provide secure data storage APIs that developers can use to store sensitive data, but many apps do not use them properly.
- Insecure communication: Mobile applications often communicate with servers over the internet to exchange data. If this communication is not encrypted, attackers can intercept and steal the data. Both Android and iOS platforms provide secure communication APIs that developers can use to encrypt data in transit, but many apps do not use them properly.
- Unauthorized access to device features: Mobile applications often require access to devise features such as the camera, microphone, or contacts list. If this access is not properly controlled, attackers can use these features to steal sensitive data or spy on the user. Both Android and iOS platforms provide APIs to control access to device features, but many apps do not use them properly.
For startup founders and entrepreneurs, ensuring the security of their mobile apps is crucial to building trust with users and protecting their businesses from the financial and reputational damage caused by security breaches. By implementing strong security measures and staying up to date on the latest security risks and vulnerabilities, businesses can help to protect their users’ data and build a more secure mobile app ecosystem.
Best practices for mobile app security against cyber attacks
Conduct a Risk Assessment:
Before developing your mobile app, it’s essential to conduct a risk assessment to identify potential security vulnerabilities and assess the potential impact of a cyber attack. This step helps you understand the security risks your app might face and allows you to develop a comprehensive security plan that addresses the specific needs of your app. A risk assessment typically involves identifying threats, vulnerabilities, and potential consequences, and assigning a level of risk based on likelihood and impact.
Implement Secure Development Practices:
Secure development practices are crucial for ensuring the security of your mobile app. Some of the best practices include using secure coding practices, encryption, and secure authentication mechanisms. Using secure coding practices involves following coding standards, avoiding common vulnerabilities such as SQL injection and cross-site scripting (XSS), and performing code reviews. Encryption is used to protect sensitive data that is transmitted between the app and the server, and also to encrypt data stored on the device. Secure authentication mechanisms, such as strong passwords, multi-factor authentication, and limiting login attempts, ensure that only authorised users can access your app.
Test Your App for Security Vulnerabilities:
Once your app is developed, it’s important to test it for security vulnerabilities. Security testing involves identifying potential vulnerabilities that could be exploited by attackers. Some common types of security testing include penetration testing, vulnerability scanning, and code review. Penetration testing involves simulating a real-world attack on your app to identify vulnerabilities. Vulnerability scanning involves using automated tools to scan your app for known vulnerabilities. Code review involves manually reviewing your app’s code to identify potential security vulnerabilities.
Monitor Your App for Security Threats:
It’s important to monitor your app for security threats on an ongoing basis. Security monitoring involves setting up security monitoring tools to detect and alert you to potential security threats. Some common types of security monitoring include network monitoring, log monitoring, and intrusion detection. Network monitoring involves monitoring network traffic to identify potential security threats. Log monitoring involves monitoring app logs for suspicious activity. Intrusion detection involves using intrusion detection systems (IDS) to detect potential security threats.
Update Your App Regularly:
Regular updates are essential for keeping your app secure. This includes updating the app itself and any third-party libraries or frameworks used in the app. Updates should be tested thoroughly before deployment to ensure that they don’t introduce new security vulnerabilities.
Secure Your App’s Backend:
In addition to securing the app itself, it’s essential to secure the app’s backend. This includes securing the server that hosts the app, as well as any APIs used by the app. Some best practices for securing your app’s backend include using secure hosting, implementing secure APIs, and using access controls to limit the data that can be accessed by different users. Secure hosting involves hosting your app on a secure server that is protected by firewalls and other security measures. Secure APIs ensure that only authorised users can access your app’s backend. Access controls are used to limit the data that can be accessed by different users.
Free Tools for Mobile App Security Testing
Startup founders and entrepreneurs must be aware that as their apps become more popular with users, hackers become interested as well. These hackers will try to exploit vulnerabilities in the apps or devices, using both manual and automated tools. To ensure that their apps are secure, developers should test them thoroughly before uploading them to app stores. Fortunately, there are several free tools available for application security testing (AST) that can help you ensure that their apps are secure. These AST tools automate the testing process, which is important as reviewing code manually against traditional threats is time-consuming, and keeping track of emerging threats adds a different level of complexity. Therefore, startup founders and entrepreneurs should consider using some of the following tools to enhance security and save time:
- OWASP Mobile Security Project: The Open Web Application Security Project (OWASP) provides a comprehensive set of tools and resources for mobile app security testing. The OWASP Mobile Security Project includes a mobile app security testing guide, a mobile app security checklist, and several mobile app security testing tools such as the OWASP Zed Attack Proxy (ZAP) and the Mobile Security Testing Guide (MSTG) app.
- MobSF: Mobile Security Framework (MobSF) is an open-source mobile app security testing framework that can be used to test both Android and iOS applications. MobSF can be used to perform dynamic analysis, static analysis, and malware analysis on mobile applications.
- AndroBugs: AndroBugs is an open-source tool that can be used to perform static analysis on Android applications. AndroBugs can detect vulnerabilities such as SQL injection, insecure storage, and insecure communication.
- QARK: Quick Android Review Kit (QARK) is an open-source tool that can be used to perform dynamic analysis on Android applications. QARK can detect vulnerabilities such as insecure storage, insecure communication, and hard-coded API keys.
- iMAS: The iOS Mobile Application Security Project (iMAS) is an open-source mobile app security testing framework that can be used to test iOS applications. iMAS can be used to perform static analysis, dynamic analysis, and jailbreak detection on iOS applications.
- Mobile Security Framework (MobSec): MobSec is a free and open-source mobile app security testing tool that can be used to test both Android and iOS applications. MobSec can be used to perform dynamic analysis, static analysis, and malware analysis on mobile applications.
These tools can help developers and security testers to identify vulnerabilities in mobile applications and implement proper security measures to protect their applications and users.
Final Thoughts
Mobile app security is essential for the success of any startup. By following the best practices outlined in this guide, you can protect your app from cyber-attacks and ensure the safety of your users’ data. Conducting a risk assessment, implementing secure development practices, testing your app for security vulnerabilities, monitoring your app for security threats, updating your app regularly, and securing your app’s backend are all important steps in ensuring the security of your app. As cyber threats continue to evolve, it’s important to stay up to date with the latest security best practices and implement them in your app development process.
Remember, the consequences of a cyber-attack can be severe and long-lasting. By prioritizing mobile app security from the start, you can protect your startup and its users from the negative impact of a security breach. Stay vigilant, stay informed, and prioritize security in your app development process.
Feel free to get in touch with us today if you want to develop a bug-free and secured mobile app for your startup.